January 28, 2026
Decentralized VPNs (dVPNs) offer better protection against correlation attacks compared to centralized VPNs. Correlation attacks analyze the size, timing, and volume of data packets to link a user's activity to their identity. Centralized VPNs rely on single servers, creating a single point of vulnerability, unlike MASQ vs. traditional VPNs which utilize decentralized architectures. If these servers are monitored or compromised, your privacy is at risk.
In contrast, dVPNs use peer-to-peer networks with multiple independent nodes, making it much harder for attackers to link your activity. Features like multi-hop routing, packet shuffling, and dummy traffic disrupt patterns that correlation attacks rely on. Additionally, dVPNs eliminate centralized logging, reducing the risk of data exposure.
Key Differences:
Centralized VPNs: Easier to use, faster speeds, but vulnerable to attacks and reliant on provider trust.
Decentralized VPNs: Prioritize privacy and censorship resistance, though they may be slower and harder to set up.
For those prioritizing privacy and anonymity, dVPNs are a stronger choice.
Centralized vs Decentralized VPNs: Security and Privacy Comparison
1. Centralized VPNs
Centralized VPNs operate under a single management system, which creates a significant vulnerability: if the provider is compromised - whether through hacking, legal demands, or internal failure - all users on the network are at risk. This setup essentially offers a single point of attack, making it an attractive target for surveillance and correlation attacks. Casey Ford, PhD, Communications Lead at Nym, sums it up:
Traditional VPNs are largely marketed on false promises. Most VPNs are not actually private at all, and one key reason for this is that they are centralized and this centralization poses major privacy risks.
Traffic Correlation Vulnerabilities
Centralized VPNs often rely on a single-hop architecture, where traffic passes through one server before reaching its destination. While this design might seem straightforward, it leaves users exposed to correlation attacks. These attacks analyze the timing and size of data packets, which are not obscured in such setups. Since centralized VPNs don’t mix or shuffle packets, attackers can easily observe traffic patterns. Marcus Eriksson, a cybersecurity analyst at Private Proxy Guide, explains:
If an attacker can watch both your ingress (ISP side) and the chosen exit simultaneously, correlation attacks (timing/size) remain feasible, especially with single-hop exits.
Research highlights the effectiveness of these attacks. For instance, correlation fingerprinting techniques can identify visited websites with an astounding 96% accuracy just by analyzing encrypted traffic patterns.
Node Control and the Trust Problem
The centralized nature of VPNs forces users to place complete trust in a single entity to handle their traffic data. This becomes even riskier as the VPN market consolidates, concentrating control into fewer hands.
Privacy Logging Risks
A common selling point for VPNs is their "no-logs" policy, but verifying these claims is often impossible. A study of 62 VPN providers revealed that 25% didn’t link to a privacy policy, and 42% of 85 providers lacked clear terms of service. Out of over 200 VPNs analyzed, only 45 explicitly stated they adhered to a "no-logs" policy. Dr. Matteo Varvello and Dr. Ben Livshits from Brave Research point out:
Users must rely on the provider's integrity.
Even when a provider claims not to log data, history shows these promises can fail under legal pressure. For example, in 2011, HideMyAss handed over logs to U.S. authorities, exposing the inherent risks of centralized control. Viktor Vecsei from IVPN elaborates on the difficulty of verifying such claims:
Centralized VPNs often fall short in demonstrating whether this condition [no activity logging] is met; open sourced applications, regular audits, and pentest reports are positive signals. Audits, however, are just a snapshot in time, and there is no way to verify the running code of a centralized service.
These vulnerabilities highlight the need to consider alternative approaches, such as decentralized architectures, to address these privacy concerns effectively.
2. Decentralized VPNs
Decentralized VPNs, or dVPNs, operate by spreading control across a network of independent nodes around the globe. Unlike traditional VPNs that route all traffic through servers owned by a single company, dVPNs create a peer-to-peer system where no single entity has full oversight. Casey Ford, PhD, Communications Lead at Nym, explains:
Decentralized VPNs aim to solve trust issues by distributing risk instead of having to put your faith into any one provider or parent company.
Traffic Correlation Resistance
One of the standout features of dVPNs is their ability to resist traffic correlation attacks. They achieve this through multi-hop routing, typically involving 2–5 nodes. Here’s how it works: the entry node can see your IP address but not your destination, while the exit node knows where you’re going but not where the traffic originated. For example, MASQ uses a 3-hop routing system that follows a Client-Origin-Relay-Exit-Server path. Thanks to end-to-end TLS encryption, exit nodes cannot decrypt the transmitted data.
Advanced dVPNs take it a step further with techniques like packet shuffling and dummy packet generation. These methods make timing analysis nearly impossible by disrupting the patterns attackers rely on. Networks like Nym shuffle packets within nodes, making it extremely difficult to link incoming and outgoing data.
Structural Unloggability
Unlike centralized VPNs that rely on "no-logs" policies, dVPNs are inherently designed to avoid centralized logging altogether. Marcus Eriksson, a cybersecurity analyst, explains this shift in trust:
A dVPN mostly shifts trust from one company to a marketplace of peers, then splits that trust across multiple hops and cryptographic protocols.
Even if a malicious node attempts to log traffic, it would only capture a tiny fraction of the encrypted path - typically less than 1% of the total network traffic. For instance, MASQ’s protocol ensures each node only has visibility into about five immediate neighbors, making it impossible for any single participant to map the entire network. VPN Gate, a volunteer-driven dVPN, demonstrates this scale with over 5,500 nodes handling more than 1 TB of traffic daily.
This decentralized structure not only reduces logging risks but also strengthens the network’s ability to resist censorship.
Censorship Resistance
The decentralized architecture of dVPNs makes them particularly hard to block. Centralized VPNs often rely on easily identifiable data center IP addresses, which governments can blacklist. In contrast, dVPNs leverage residential IP addresses from node operators worldwide. Blocking these addresses risks disrupting regular internet users, making censorship efforts more challenging. Dr. Matteo Varvello and Dr. Ben Livshits from Brave Research highlight this advantage:
The large and heterogenous footprint of dVPNs make [service outages] more unlikely.
If certain nodes are blocked or go offline, the network automatically reroutes traffic through available nodes. This adaptability is further supported by blockchain-based incentives. For example, MASQ rewards node operators with MASQ tokens for sharing bandwidth, with 3-hop routing consuming an average of 700–1,000 GB per 1 MASQ token.
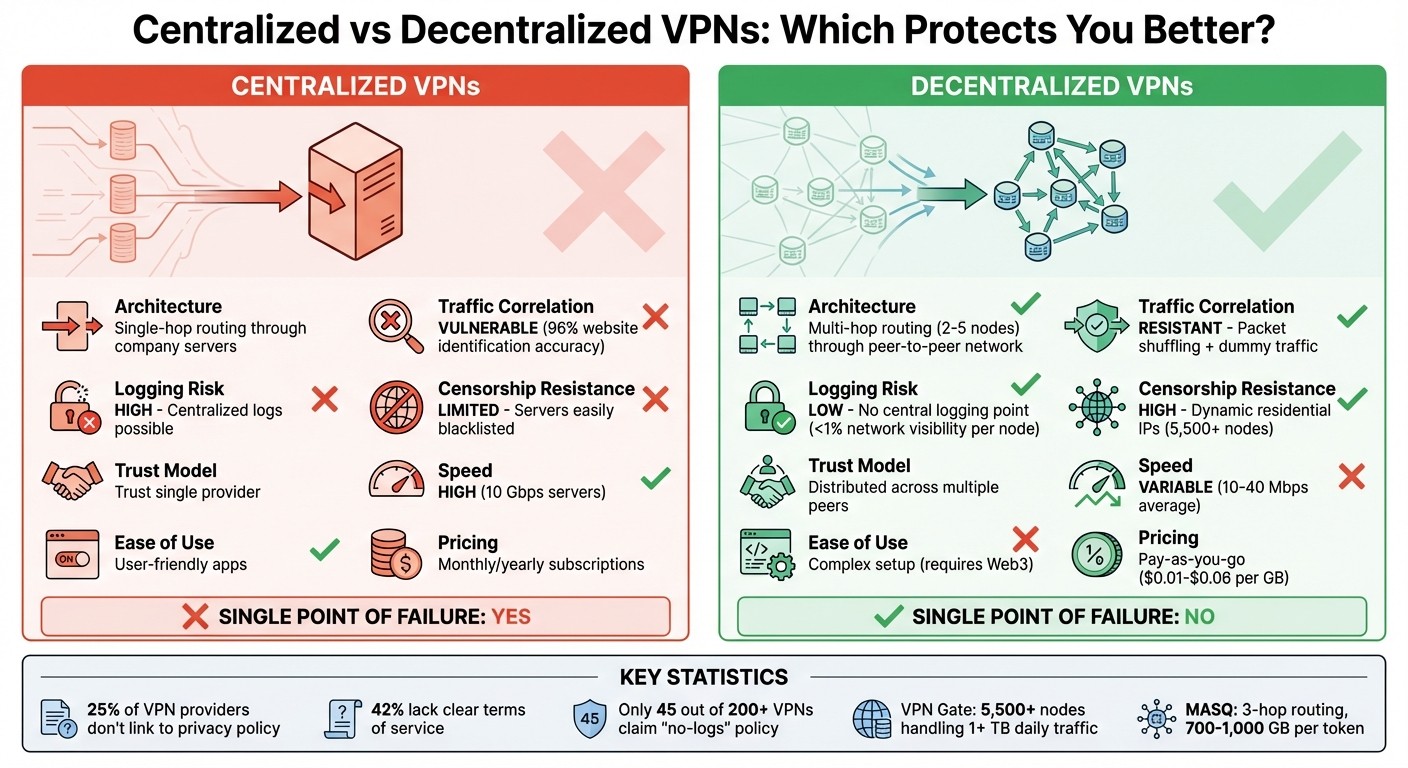
Feature | Centralized VPNs | Decentralized VPNs |
|---|---|---|
Traffic Correlation | Vulnerable to timing/size analysis due to single-hop | Resistant via multi-hop, packet shuffling, and dummy traffic |
Logging Risk | High (Centralized logs possible) | Low (No central logging point) |
Censorship Resistance | Limited; servers easily blacklisted | High; dynamic nodes and residential IPs |
Trust Model | Trust in a single provider | Trust distributed across multiple peers |
Pros and Cons
Centralized VPNs are known for their high speeds, intuitive apps, and dedicated customer support, making them excellent choices for activities like streaming and gaming. However, they come with a significant trade-off: you must trust a single company to handle your data responsibly.
On the other hand, decentralized VPNs focus heavily on privacy by utilizing a distributed network. This architecture makes it significantly harder for any single entity to track or log your activity. They also excel at bypassing censorship, as blocking all residential nodes would disrupt regular internet users. Decentralized VPNs typically operate on a pay-as-you-go model, costing around $0.01 to $0.06 per GB, rather than relying on recurring subscriptions. However, they do have drawbacks. Speeds are generally slower, averaging between 10 and 40 Mbps due to multi-hop routing and reliance on residential nodes. Additionally, setting up a decentralized VPN can be more complicated, often requiring a crypto wallet and the handling of transaction fees.
Here’s a side-by-side breakdown of the key differences:
Aspect | Centralized VPNs | Decentralized VPNs |
|---|---|---|
Speed | High and consistent (10-Gbps servers) | Variable (10–40 Mbps average) |
Privacy | Relies on provider's "no-logs" policy | Built-in privacy; no central logging |
Ease of Use | User-friendly apps; beginner-friendly | Complex setup; requires Web3 knowledge |
Customer Support | 24/7 dedicated support teams | Limited or community-based support |
Censorship Resistance | Moderate; servers can be blocked | High; uses distributed residential IPs |
Pricing Model | Monthly/yearly subscriptions | Pay-as-you-go (via crypto tokens) |
Single Point of Failure | Yes (provider's servers) | No (distributed network of nodes) |
Ultimately, your choice depends on what you value most. If you’re looking for ease of use and high performance, centralized VPNs are a straightforward option. But if privacy, censorship resistance, and anonymity are your top priorities - especially in regions with strict internet controls - decentralized VPNs like MASQ stand out with their multi-hop routing and token-based payment systems.
Conclusion
Decentralized VPNs are reshaping online privacy by offering a fundamentally different approach to securing your data. Instead of relying on a single corporate server, these systems route traffic through multiple independent nodes, ensuring no single entity can see both your IP address and your destination. As cybersecurity analyst Marcus Eriksson puts it:
A dVPN mostly shifts trust from one company to a marketplace of peers, then splits that trust across multiple hops and cryptographic protocols.
This decentralized structure makes correlation attacks virtually impossible. Advanced features, like shuffling data packets and inserting dummy traffic, effectively counter timing analysis. What’s more, decentralized networks don’t rely on a central database, eliminating the risk of hacking, subpoenas, or data breaches.
But the benefits don’t stop there. Decentralized VPNs also strengthen network resilience and are particularly effective at resisting censorship. Their dynamic, ever-changing architecture makes blocking access a significant challenge for restrictive regimes.
For those seeking secure and private internet access - especially in areas with heavy surveillance or censorship - decentralized VPNs stand out as a strong choice. Take MASQ, for example. It embodies the decentralized model with multi-hop routing, Web3 integration, and flexible pay-as-you-go pricing starting at $7 per month.
Ultimately, the decision is simple: you can either place all your trust in a single company or spread it across a network built to prioritize your privacy by design.
FAQs
Why are decentralized VPNs better at protecting against correlation attacks than traditional VPNs?
Decentralized VPNs stand out when it comes to protecting against correlation attacks. Instead of depending on a central server, they run on a peer-to-peer network made up of distributed nodes. This setup makes it significantly harder for anyone to trace your data back to its source or spot patterns in your online activity.
One standout feature is multi-hop routing, which routes your data through multiple encrypted nodes before it reaches its destination. This adds an extra layer of anonymity. Plus, because decentralized VPNs avoid keeping centralized logs, there’s no single point of failure or storage for attackers to target. This structure ensures that your online activity stays private and secure, even against advanced tracking techniques.
What makes decentralized VPNs more secure than traditional VPNs?
Decentralized VPNs, or dVPNs, take online privacy and security to the next level by removing the need for a central authority. Unlike traditional VPNs that rely on a centralized server setup, dVPNs operate on a peer-to-peer network. Here, your internet traffic is spread across multiple independent nodes, eliminating single points of failure. This also means there are no central logs or data repositories that could be vulnerable to breaches.
What makes dVPNs even more appealing is their resistance to censorship and surveillance. Thanks to their distributed structure, it’s incredibly difficult for any single party to block or monitor all user activity. Many dVPNs also incorporate multi-hop routing, which encrypts your data as it passes through several nodes. This makes it significantly harder for anyone to trace your online activity through traffic correlation attacks. For those navigating heavily monitored or restricted online environments, decentralized VPNs offer a powerful solution for safeguarding privacy and accessing blocked content.
Are there any downsides to using decentralized VPNs compared to traditional ones?
Decentralized VPNs, or dVPNs, offer a fresh approach to online privacy and security by removing the need for centralized servers. However, they come with a few challenges. For starters, setting up and using a dVPN often demands a bit more technical know-how. If you're not familiar with peer-to-peer networks or blockchain technology, it might feel a bit daunting.
Another thing to consider is performance. Since dVPNs operate on a network of independent nodes, speeds can sometimes be less predictable compared to traditional VPNs, which rely on optimized server setups. There's also the question of reliability - peer-operated nodes might not always inspire confidence, and there's always the slight risk of encountering bad actors within the network.
That said, dVPNs are a solid option for those who value privacy and want to bypass censorship. While they might not yet offer the same user-friendly experience or polished design as some centralized VPN services, they’re a standout choice for anyone prioritizing decentralized solutions and online freedom.




