December 15, 2025

P2P anonymous communication is reshaping online privacy by decentralizing data flow and protecting users from surveillance. Unlike traditional VPNs, these systems use distributed nodes to mask IP addresses, hide metadata, and resist censorship. Key technologies include onion routing, multi-hop paths, encrypted overlays, and mixnets, which together make tracking nearly impossible. Tools like MASQ combine these features with Web3 integration, offering privacy-focused browsing, tokenized bandwidth sharing, and access to decentralized applications.
Key Takeaways:
Privacy: Masks IPs, secures metadata, and avoids centralized tracking.
Censorship Resistance: Dynamic routing through global nodes bypasses restrictions.
User Benefits: Earn tokens by sharing bandwidth, access geo-blocked content, and protect sensitive data.
Advancements in routing, traffic obfuscation, and anti-fingerprinting are making these tools more effective. While slower than traditional networks, they offer unmatched privacy and freedom in an era of increasing surveillance.
Core Technologies and Challenges in P2P Anonymity
Key Technologies Enabling P2P Anonymity
Peer-to-peer (P2P) anonymity relies on a combination of advanced technologies like end-to-end encryption, onion routing, multi-hop routing, distributed hash tables (DHTs), and mixnets. Let’s break these down:
End-to-end encryption: This method, often using asymmetric PGP keys, ensures that both the content of messages and session data remain secure. Since the encryption keys stay on your device, it prevents interception or tampering, protecting both the message itself and the surrounding metadata.
Onion routing: Data is encrypted in multiple layers as it travels through various nodes. Each node only knows the previous and next stops in the chain, never the full route. This creates a zigzag-like path that makes tracking extremely difficult.
Multi-hop routing: By sending traffic through several peers, this approach obscures the origin even further.
Distributed hash tables (DHTs): These facilitate decentralized resource discovery without the need for a central directory. However, DHT lookups can inadvertently expose information, leaving users vulnerable to passive attackers who may exploit these queries to identify them.
Mixnets: These networks shuffle and batch messages from multiple users, making it significantly harder to match senders with receivers, thereby mitigating traffic analysis.
MASQ integrates these technologies into its decentralized VPN framework. By employing multi-hop routing, MASQ ensures that no single node has complete knowledge of the data flow, removing the central point of trust that traditional VPNs rely on. While these tools are powerful, they are not without risks, as outlined below.
Threats to P2P Anonymity
Even the most advanced P2P systems face serious challenges in real-world scenarios:
ISP logging: Internet service providers can log metadata, creating a record of communications that could reveal patterns and routines over time.
Traffic fingerprinting: Even with encryption, attackers can analyze packet sizes, timing, and data flow to identify users.
State-level censorship: Governments may block P2P nodes or enforce SIM registration, linking online activity to specific individuals.
Corporate tracking: Data brokers and advertisers monitor user behavior across websites and apps to build detailed profiles.
Additionally, structured P2P systems face risks from information leaks during resource lookups. For instance, when querying a DHT, passive attackers might observe these requests. Research on systems like Salsa and AP3 shows that while defenses against active attacks are effective, they can sometimes inadvertently increase vulnerability to passive attacks, creating a tricky balance to maintain.
Everyday Use Cases
Despite these challenges, P2P anonymity technologies address several privacy needs for everyday users in the United States:
Blocking data harvesting: Tools like MASQ include ad and tracker blocking features that prevent ad networks and data brokers from collecting browsing data.
Securing remote work traffic: Professionals working remotely often need to protect sensitive business information. Features like multi-hop routing and dynamic identifiers help obscure communication patterns and operational details.
Accessing geo-restricted content: Many users rely on P2P networks to bypass regional content restrictions on streaming platforms or websites. Unlike traditional systems that depend on central servers, P2P networks are more resistant to ISP blocks. MASQ’s Country Switching Mode allows users to route traffic through different regions, effectively bypassing restrictions while maintaining privacy through its decentralized design.
Future Developments in P2P Anonymous Communication
Network-Layer Advancements
The future of peer-to-peer (P2P) anonymity is heading toward smarter, more adaptive routing systems. These systems will select relay paths dynamically, factoring in latency, legal jurisdictions, and trust scores to unlink the origin and destination of data. Unlike fixed routes, these advanced systems will adjust in real time to dodge censored regions and unreliable nodes, ensuring smoother and more secure communication.
Another major focus is traffic obfuscation. Emerging protocols are designed to disguise P2P traffic as everyday HTTPS or QUIC connections, making it much harder for deep packet inspection tools to identify and block these connections. By blending into regular web traffic, these advancements help privacy tools stay effective even when internet service providers (ISPs) or workplace networks attempt to restrict them.
Distributed hash tables (DHTs) are also getting a much-needed security overhaul. Earlier systems like Salsa and AP3 revealed vulnerabilities where lookup queries could leak enough information to compromise user anonymity. To counter this, the next generation of DHTs will employ techniques like randomizing path selection and limiting routing table visibility. These changes aim to reduce information leaks and make passive surveillance significantly less effective.
These network-level improvements are setting the stage for more advanced privacy tools, especially at the application level.
Privacy-First Browsers and Decentralized Tools
Capitalizing on these routing advancements, privacy-focused browsers are evolving into powerful tools that go beyond simple tracker blocking. These browsers now combine multi-hop routing, tracker prevention, and Web3 integration to enhance user anonymity. Instead of relying on centralized servers, they connect users to decentralized peer-to-peer networks, distributing trust across numerous nodes.
For instance, MASQ’s browser integrates features like tracker blocking, multi-hop traffic routing, and support for Web3 wallets. It also allows users to access censorship-resistant content by resolving ENS domains and IPFS URLs - something traditional browsers often can’t handle.
Anti-fingerprinting measures are becoming another standard feature. These defenses randomize high-entropy attributes such as canvas rendering, audio signatures, and font lists, making it harder for websites to create a consistent profile of your device - even when cookies are disabled. This is critical as advertisers and data brokers increasingly turn to fingerprinting to bypass other privacy safeguards.
To complement these privacy features, economic incentives are being introduced to strengthen the network.
Tokenized Bandwidth Sharing and Economic Incentives
Tokenized bandwidth-sharing models are addressing the long-standing issue of free-riding in P2P networks. By earning tokens for operating relay nodes and forwarding encrypted traffic, users are incentivized to maintain high-speed, reliable nodes. This approach encourages the creation of a geographically diverse relay pool that is far more difficult for censors to block entirely.
In MASQ’s network, for example, U.S.-based users can earn tokens by forwarding traffic. These tokens can then be used to pay for private routing services or traded in Web3 marketplaces. To participate effectively, users need stable broadband connections, unrestricted networks, and automatic updates enabled.
This token-based model not only discourages free-riding but also makes the network more resilient. With thousands of incentivized users contributing, it becomes nearly impossible for censors to block all relay nodes. Even if some nodes are taken offline, the network can quickly adapt by rerouting traffic. Additionally, the sustainable funding provided by this system supports ongoing protocol improvements without relying on centralized subscription fees.
These advancements are paving the way for stronger anonymity, better censorship resistance, and greater control over online privacy for users everywhere.
Introducing Quiet - Encrypted P2P team chat without servers, just Tor - Holmes Wilson
Using P2P Tools to Bypass Censorship and Protect Privacy
Centralized VPNs vs P2P Anonymous Networks Comparison
Censorship Tactics and the Challenges of Centralized Tools
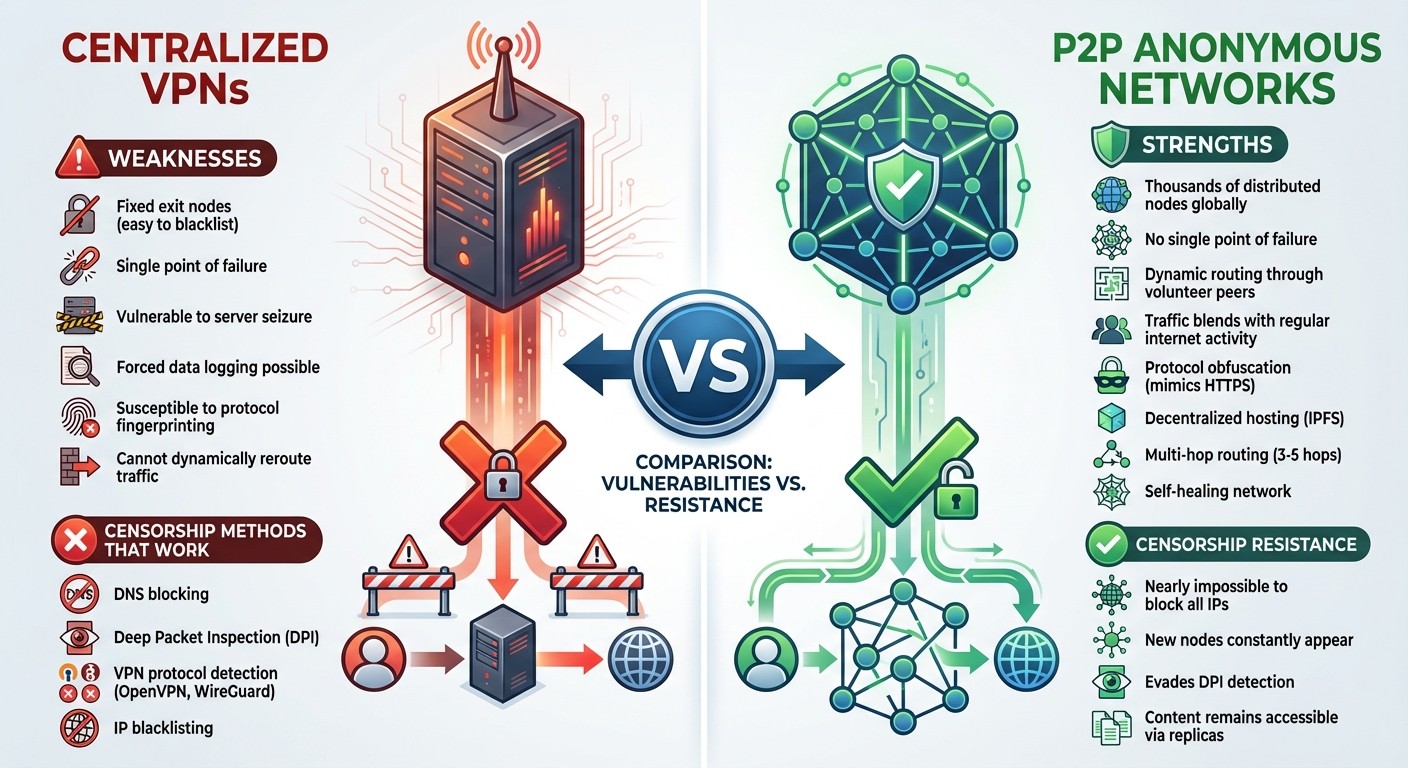
Censorship often relies on methods like DNS blocking, which stops domain names from resolving to specific sites; deep packet inspection (DPI), which scans internet traffic for keywords, protocols, or patterns to block or throttle specific content; and VPN bans, where known VPN protocols like OpenVPN or WireGuard are detected and blocked. In more restrictive environments, DPI can identify VPN signatures and shut them down entirely.
Centralized VPNs, while helpful, come with vulnerabilities. They use fixed exit nodes, which are easy targets for blacklisting. If these servers are seized or forced to log user data, privacy is immediately at risk. Unlike distributed systems, centralized tools lack the ability to reroute traffic dynamically through thousands of volunteer nodes. This makes them more susceptible to protocol fingerprinting and surveillance attacks. Decentralized P2P systems, however, take a different approach, offering a more resilient solution.
How P2P and Web3 Technologies Fight Back Against Censorship
P2P networks combat censorship by routing traffic through distributed nodes - thousands of volunteer peers spread across the globe. This decentralized setup makes it nearly impossible to block all IPs, as new nodes constantly appear in different regions. Additionally, the traffic in these networks blends in with regular internet activity, evading detection by DPI. For example, I2P (Invisible Internet Project) uses encrypted overlays that obscure content, ensuring the network remains functional even if some nodes are compromised.
Protocol obfuscation further strengthens P2P networks by disguising their traffic to look like standard HTTPS traffic, making it harder for censors to identify and block. Meanwhile, decentralized hosting platforms like IPFS ensure content stays accessible even if some nodes are taken offline. If one node goes down, replicas on other nodes keep the content available.
MASQ's Contribution to Privacy and Freedom

MASQ builds on these strategies to offer a robust solution for privacy and censorship resistance. By routing connections through multiple hops (starting with 3 by default and up to 5 for premium users), MASQ creates a complex, zigzagging path that makes it extremely difficult to trace the origin or destination of data. Its distributed architecture eliminates the weak points found in centralized VPNs, ensuring a higher level of security and privacy.
The MASQ browser integrates its decentralized VPN (dVPN) with features like automatic ad and tracker blocking, Web3 wallet support, and access to decentralized applications via its dApp store. For users in the US dealing with corporate surveillance or regional content restrictions, MASQ allows access to geo-blocked streaming services and censored websites without leaving a traceable digital footprint. Moreover, its tokenized bandwidth-sharing model encourages users to share their internet connections, earning $MASQ tokens while simultaneously strengthening the network’s ability to resist censorship.
Practical Considerations for Adopting P2P Privacy Tools
Legal and Ethical Aspects
When it comes to privacy tools like VPNs and P2P networks, it's important to navigate the legal and ethical landscape carefully.
In the United States, VPNs and P2P privacy tools are entirely legal for personal privacy protection - there are no federal restrictions on their use. However, using these tools for illegal activities, such as violating copyright laws under the DMCA or evading law enforcement, can lead to serious legal consequences. The tools themselves aren't the problem; it's how you use them that determines legality.
Laws like the PATRIOT Act and the CLOUD Act grant the government access to metadata from ISPs and tech companies. That said, P2P tools designed to minimize metadata collection remain within legal bounds as long as they're not used to hide criminal activity. For users of decentralized Web3 wallets, there's no KYC (Know Your Customer) verification required, unlike centralized platforms. However, keep in mind that the IRS mandates reporting any cryptocurrency gains over $600 annually. If you're earning MASQ tokens through bandwidth sharing in MASQ's ecosystem, make sure to account for those earnings to avoid tax penalties.
From an ethical standpoint, use P2P tools responsibly. Legitimate uses include protecting yourself from corporate surveillance, accessing geo-restricted content, and ensuring the privacy of sensitive communications. However, anonymity should never be a shield for harassment or fraud. For professionals, especially executives, transparency is key - if you're using anonymized communication, consider disclosing your practices to maintain trust. These guidelines emphasize the importance of using P2P tools for privacy, not exploitation.
Security Best Practices
Securing your device is the first step to safeguarding your privacy. Start by enabling BitLocker for encryption, keeping your firewall active, and avoiding public Wi-Fi without protection. Regularly update your software to close security gaps that attackers might exploit. For P2P networks, asymmetric encryption like PGP ensures your private keys remain on your device, reducing the risk of metadata exposure.
When managing Web3 wallets, exercise caution. Store significant amounts of MASQ tokens in hardware wallets like Ledger and use multi-signature protection for high-value assets. Always back up your seed phrases offline - don't store them digitally or in the cloud - and rotate your wallets periodically to prevent profiling. Before engaging with any dApp in MASQ's decentralized store, verify the smart contracts using tools like Etherscan.
P2P networks come with their own challenges. Information leaks from lookup mechanisms can expose users to passive attacks. MASQ addresses this with multi-hop routing, which creates intricate paths to obscure identity links. By default, MASQ includes privacy features like ad and tracker blocking, and it’s a good habit to clear your digital footprint regularly. With these measures in place, you can focus on balancing privacy with performance and cost.
Performance and Cost Expectations
Privacy comes with trade-offs, especially in speed. Multi-hop routing adds 100-500ms per hop, and download speeds can drop to 10-50% of your usual rate - typically around 5-20 Mbps on standard consumer hardware. While this setup isn’t ideal for 4K streaming, it works well for browsing, messaging, and bypassing censorship. Surveys show that 40-60% of US privacy tool users report speed reductions of 20-50% when using multi-hop routing, with about 25% abandoning the tools due to latency issues.
MASQ offers a flexible cost model through its token system. By sharing bandwidth, users can earn MASQ tokens, averaging $0.50-$2.00 daily on typical US connections with speeds over 100 Mbps. These tokens can offset network usage costs, which range from 0.1-0.5 MASQ per GB. For those seeking premium features like multi-hop routing (up to 5 hops), faster speeds, and country selection, MASQ Premium costs $8/month (billed annually) or $14/month. Alternatively, the pay-as-you-go option lets users top up their wallets without committing to a subscription. Initial hardware wallet costs range between $50 and $200, but the earning potential makes this system more cost-effective than traditional VPNs, which typically charge $5-$15/month without offering any earning opportunities.
Conclusion: The Future of P2P Anonymous Communication
In the United States, privacy faces growing threats from mass data collection and AI-powered surveillance. Encrypting your messages is a start, but if metadata isn’t protected, your activity can still be traced and analyzed. Even with encryption, metadata can reveal patterns and profiles, leaving users vulnerable.
Centralized systems come with their own risks, acting as single points of failure. In contrast, peer-to-peer (P2P) overlays and multi-hop routing distribute traffic across independent nodes, making censorship and compromise far more challenging. A great example of this is MASQ, which leverages multi-hop routing (up to five hops for premium users), a decentralized node network, and integrated Web3 features designed to adapt to ever-changing censorship tactics.
These technical advancements are more than theoretical - they’re making a real difference in everyday privacy and freedom. P2P tools like these allow users to bypass geo-restrictions, discuss sensitive topics without exposing personal data to trackers, engage with Web3 ecosystems through built-in wallets and dApp stores, and even earn MASQ tokens by sharing bandwidth. This creates a self-sustaining system where users actively contribute to maintaining privacy and free access.
To get started, think about your specific privacy needs and look for reliable tools like MASQ that combine strong device security, tracker blocking, and P2P routing. Begin with safer activities like streaming or accessing restricted content to test the waters, and always keep your software up-to-date to guard against emerging threats to anonymity.
FAQs
How do peer-to-peer (P2P) anonymous communication systems provide better online privacy than traditional VPNs?
Peer-to-peer (P2P) anonymous communication systems take online privacy to a higher level by decentralizing how data is routed. Instead of relying on a single, centralized server, these systems use a network of multiple nodes to transmit data. This approach, known as multi-hop routing, makes it significantly more challenging for third parties to track or monitor your online activity.
On the other hand, traditional VPNs depend on centralized servers, which can act as weak points if they’re monitored, censored, or even compromised. P2P systems distribute traffic across the entire network, making them more resilient against surveillance and a better option for maintaining privacy or bypassing censorship.
What challenges and risks come with using P2P anonymous communication technologies?
While P2P anonymous communication technologies offer greater privacy and freedom online, they aren’t without their hurdles. One issue is the risk posed by malicious nodes within the network. These harmful actors could potentially compromise user privacy or security, undermining the very anonymity the system aims to provide.
The multi-hop routing system, a cornerstone of anonymity in these networks, can also be a double-edged sword. While it enhances privacy, it often results in slower connection speeds and increased latency, which can impact the overall user experience.
Another concern revolves around the security of shared bandwidth. Users who contribute their internet resources to the network may face exploitation if adequate safeguards aren’t in place. On top of that, evolving regulations targeting decentralized privacy tools could create legal gray areas, especially in countries with strict censorship or heavy surveillance laws. To navigate these challenges, it’s crucial to stay informed and rely on trusted, secure platforms.
What is tokenized bandwidth sharing, and how does it work in P2P networks like MASQ?
Tokenized bandwidth sharing in MASQ's peer-to-peer network gives users the ability to share their internet bandwidth and earn MASQ utility tokens as a reward. The number of tokens earned is directly tied to how much bandwidth a user shares and their level of activity within the network.
This approach encourages users to contribute their resources, which bolsters the network’s decentralization, improves privacy, and builds a stronger ecosystem for secure and anonymous communication.




